In WLAN we have 3 diffrent power save modes
1. Legacy power save mode
2. WMM power save mode
3. 11N power save mode
1. Legacy Power Save mode
- AP will manage the legacy power save mode clients by using the element id "Traffic Indication Map(TIM)".
- The TIM shall identify the STAs for which traffic is pending and buffered in the AP. This information is coded in a partial virtual bitmap.
- TIM contain DTIM count and DTIM period for Multicast and Broadcast traffic.
- It will make use of "Traffic Indication Bit" , "Bit Map Offset" and "Partial Virtual Bmap" .
- Every AP will have constant DTIM period and DTIM count will decrement for every Beacon.Whenever DTIM count reaches zero all the clients which are connected to that AP will wake up from Dozzing state.
- AP will send all Broadcast/Multicast traffic that is buffered in the AP.
- Every STA is assigned an AID by the AP as part of the association process.
- AID 0 (zero) is reserved to indicate the presence of buffered broadcast/multicast MSDUs.
- The AP shall identify those STAs for which it is prepared to deliver buffered MSDUs by setting bits in the TIM’s partial virtual bitmap that correspond to the appropriate AIDs.
See below Diagram for the reference.
See below picture for your reference for TIM in Beacon
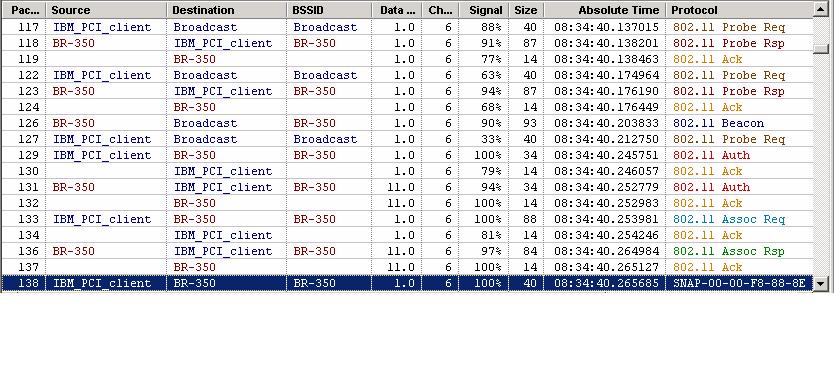
In Legacy mode client will negotiate the "Listen interval" at the time of Association request. See below frame exchange in open authentication.
See below Association Request Frame which contains listen interval that will be negotiated during connection establishment.
- The client waits in receiving mode for a beacon frame from the base station.
- The beacon frame includes Traffic Indication Map (TIM) information that tells the client whether there is any data available for download.
- If there is no data to download, the client can doze until the next beacon frame.
- If there is data available, the client sends a PS-Poll (Power Save–Polling) frame to request a download of the data. After sending an acknowledgement frame, the access point starts transmitting frames with the data.
See below frame exchanges with PS-Poll messages.
- For each frame, the client sends a PS-Poll frame and an acknowledgement frame after the data has been received and receive an acknowledgement of its download request.
- When the access point has downloaded the data to the client, it sends a bit in the last data frame that indicates it is the last. Upon receiving this, the client goes back to dozing mode.
Dis-advantages:
- A DCF (Distributed Coordination Function) delay is imposed between any two frames sent by the access point or the client, regardless of the type of traffic (e.g., voice, email downloading, or Internet browsing).
- As a result, for each data frame sent from the access point, two data frames are sent from the access point and from the client, and two DCF access delays are interleaved.
- Legacy power save operates in a ping-pong fashion that increases the latency for applications that require frequent data exchanges between the client and the access point, like VoIP, or voice and audio streaming.
- The client has to wait for the beacon frame and cannot initiate transmission at shorter intervals.
- Only one data frame is sent at a time and the client has to transmit and receive additional signalling frames for each data frame received.
- The dozing time is set by the client Wi-Fi driver regardless of which applications it runs, thus limiting the opportunity to tailor the client behaviour to the requirements of specific applications.
WMM power save mode and 11N power save will cover in separate topics.