For connecting the client to AP with 802.1x involves sequence of steps.
Below are sequence of steps.
1. Client started with Active scanning . Sends "Probe request"
2. AP responds with "Probe Response"
3. Client sends "Auth Request"
4. AP responds with "Auth Response"
5. Client sends "Assosiation Request"
6. AP responds with "Assosiation Resonse"
7. The station sends an "EAPOL - Start" message to the AP.This initiates the process of "EAP authentication".
8. The AP sends an "access request" on behalf of the client to the RADIUS server.
9. The AP replies with an "EAP Request/Identity" message.
10. The station sends an "EAP Response/Identity" message containing its credentials (such as username) to the AP. This
message will contain ID based on the EAP type such as "EAP-TLS", "EAP-TTLS", "EAP-PEAP", "EAP-LEAP", or "EAP-FAST".In a password-based EAP, the user.s password is NOT part of this
message.
11. The AP forwards the "user ID" to the "RADIUS server".
12. The "RADIUS server" responds with a "challenge message", which the access point forwards to the station as an EAP message.
13. The station encrypts the challenge message using its password (or other credential) as a secret key and sends the resulting value back to the AP.
14. The access point forwards the "encrypted challenge" to the "RADIUS server".
15. The RADIUS server uses the password (or other credential) that it has stored for the user to encrypt the same challenge message it sent to the station. If the resultant value and the value returned by
the station match, the RADIUS server sends a success message to the AP.
16. The AP forwards the "success/failure" message to the station.
17. The station now sends a "challenge" to the "RADIUS server" to authenticate the AP (the network), and proceeds through the reverse authentication process.
18. If the network is successfully authenticated, the station passes a success message through the AP to the RADIUS server, which opens a port. The user is now LIVE on the network.
19. The station and RADIUS server each generate a dynamic unicast key (which will match) from key material exchanged during the mutual authentication phase.
20. The RADIUS server sends the unicast WEP key to the AP in a RADIUS attribute. The attribute is encrypted using the shared key used between the AP and RADIUS server.
21. Now Client sends "DHCP" discover message if it is configured for DHCP IP address.
22. DHCP servers will respond with "DHCP offer " messages.
23. Client will respond for one of the "DHCP offer" Messages with "DHCP request"
24. Then corresponding "DHCP server" responds with "DHCP ACK" message for confirmation.
25. Now client is able to send data to the AP network.
 Please see the above frame exchange for the sample
Please see the above frame exchange for the sample 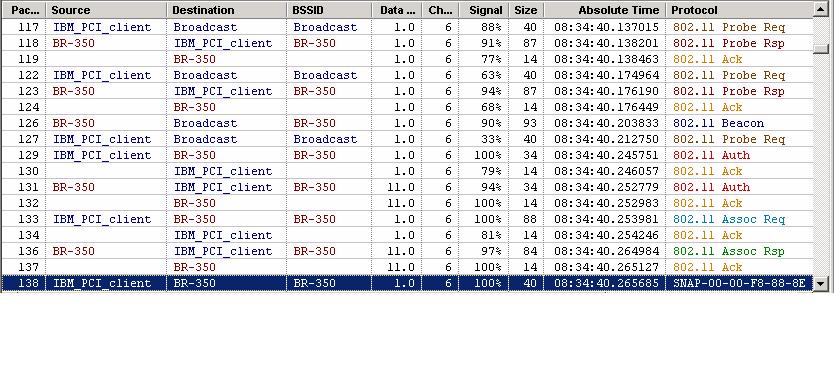
think , if u add the details about security stuff it will be too good,
ReplyDeleteex: how to configure wep,wpa-psk etc..
Configuring the security will vary depend on AP and depend on the client. If you need any specific AP i can help you.
DeleteHi, i have a very basic question about Passive scaning.
ReplyDeletehow did you simulate a test scenario of "wireless client connecting to a AP using passive scanning method" ?
please share your idea on this.
thank you
Kumar.
Hi Naga,
ReplyDeleteReally wonderful information, I appreciate your work.
Thanks,
Kabilan
Hi Naga,
ReplyDeleteGood Info............
Thanks for sharing.
Thanks
Ravi Teja
Hi Sir,
ReplyDeleteCan you please explain, why we need two types of scanning (Active/Passive) in 802.11
Also, i observe there're 3-4 action frames after successful authentication. Are these action frames are for DHCP req/res or some other negotiation happening. It would be great if you can explain. Thanks in advance.
ReplyDeleteAction frames may be for 11n related like BA request or may be WMM related. Action frames not used for DHCP.
Deletehii Nagababu,
ReplyDeletePlease rectify the below, instead of EAP-Start it should be EAPOL Start.
7. The station sends an "EAP - Start" message to the AP.This initiates the process of "EAP authentication".
Wow great work brother you explained all steps very well. I got solution of many problems that I’m facing in connection client top AP. It’s really helpful for me.
ReplyDeleteNice blog and useful and interesting information about the Global Empowers it's really good work.
ReplyDeleteNice blog i like this one.
ReplyDeletenice blog
ReplyDeleteThank You For Sharing this Post . It will be Helpful in Future in the field of Tech @ Support D - Link Costumer Service
ReplyDelete